High Availability is usually performed in most of the data centers networks today which ensures application availability . High Availability is usually achieved in case one of the appliance goes down or have some physical or logical connectivity issues.
Achieving high availability in Palo Alto firewall is relatively very easy. Palo Alto firewall can work in both Active/Standby mode or in Active/Active. We will basically be talking about Active/Standby mode in this article. There are basically two links that needs to be configure in Palo Alto for HA.
1. Control Links
Control Links are associated with control plane traffic which is mainly used for heartbeat exchanged, configuration synchronization. Dedicate HA ports are available in higher series of Palo Alto or even a HA interface can be created for some inband ports.
2. Data Links
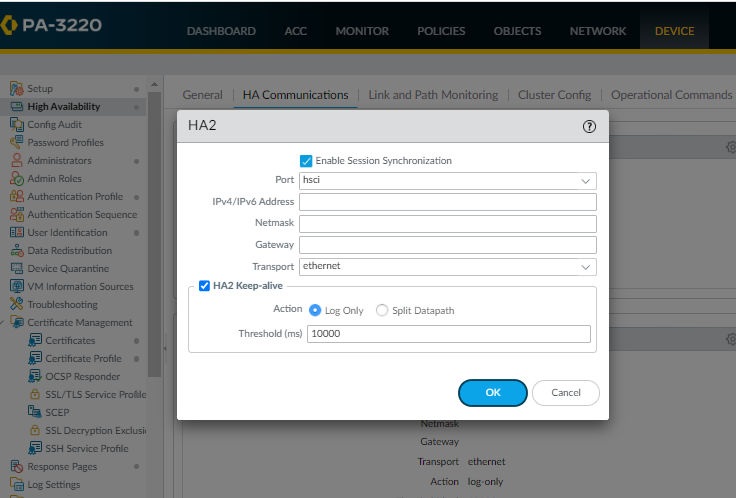
Data Links are mainly used for session synchronization, forwarding table synchronization. Dedicated HSCI Ports are available for higher end Palo Alto whereas as mentioned earlier inband ports can also be used.
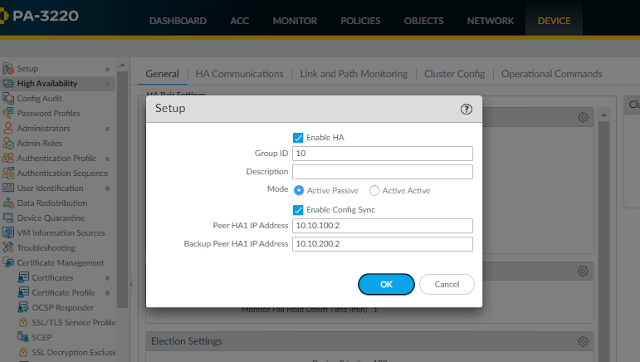
- Control Link needs to be configured with a point to point IP and Data Link can be configured with IP, ethernet or UDP as a transport connection.
- Group ID also needs to be mentioned with group id being same on both the boxes.
- Mode will be Active/Passive.
- Device Priority with lesser number will be in active state.
- Preemption must be enabled only on the primary device.
- Inband data ports can also be as High Availability ports for control link , data link as well as for backup links





Comments
Post a Comment